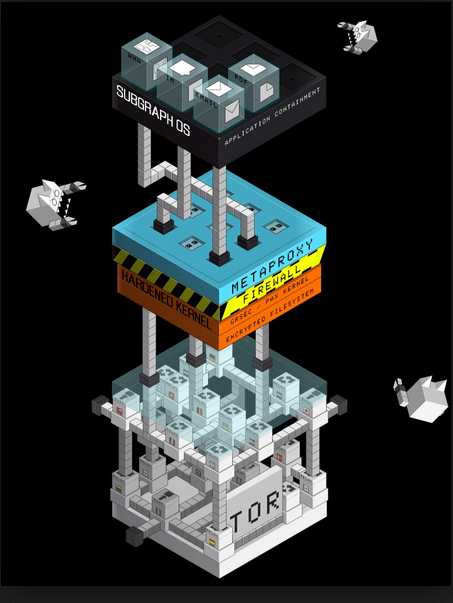
Increased security often comes at a price in Linux distributions. Tails, for example, allows anonymous browsing at the cost of running from a flash drive. Similarly, Qubes OS provides comprehensive security but with an enormous increase in memory requirements. By contrast, Subgraph OS (SGOS) increase security by installing existing security features that other distributions leave out, adding graphical access to them at a cost no higher than some extra configuration after installation.
The maker of SGOS is Subgraph, an open source security company based in Montreal, Canada. Subgraph is also the developer of Vega, a web application security testing tool, and Orchid, a Java Tor client. SGOS itself is a Debian-derivative running a GNOME desktop environment, and currently in a usable if somewhat rough alpha release.
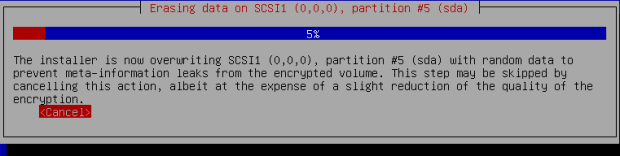
SGOS uses the standard Debian installer, with options for a Live Disk, and a standard or advanced installation. The standard install differs from Debian’s chiefly in the fact that disk encryption is mandatory and that partitions are over-written with random data before set up before installation — a process that can be skipped, but at the cost of some unspecified loss os security. Somewhat surprisingly, it enforces strong passwords or passphrases only by the number of characters, although whether that is due a conviction that passwords are weak security, or of less concern with disk encryption is uncertain. Or possibly SGOS will enforce passwords that include characters and a variety of cases in later releases.
Basic Software Selection
In order to create secure packages, SGOS — at least so far — includes only a limited set of packages. Within these packages, an inexperienced use logged into SGOS might notice very few differences from any modern GNOME installation. Superficially, productivity tools like LibreOffice can be used without any differences being noticed at all. Even the appearance of such standard privacy tools like BleachBit or the data manager KeePassX is not particularly unusual, although an interface designer might observe a preference for desktop tools with simple interfaces.
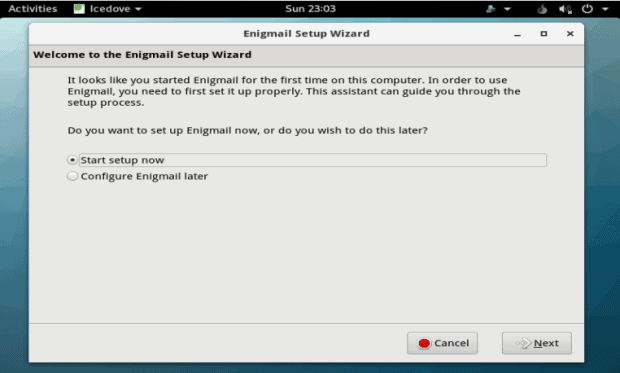
However, the more users explore, the more they will discover built-in security features. For example, the file manager includes extra menu items for encrypting, signing, or wiping files. Similarly, a standard browser is replaced by a Tor browser for anonymous web browsing, while Icedove (Debian’s non-trademarked name forThunderbird) opens ready to set up Enigmail, the plugin that the Free Software Foundation recommends for sending encrypted email . Both Tor and Enigmail, of course, can be downloaded on other distributions, but, seeing them in SGOS, a blinding flash of the obvious makes me wonder why, if security is so important, they are not part of the default installation in most distributions? Ten minutes spent configuring each of them seems a small price for increased security.
Users may miss the Subgraph metaproxy, which prevents more than one tool going out over the Tor circuit and potentially compromising security. And, almost certainly, they will fail to notice without running through the source code the prescence of a series of kernel patches that the company has named GrSecurity. However other clues, such as CoyIM, a new security-hardened instant messenger, or the self-explanatory Metadata Anonymisation Toolkit, will leave little doubt of SGOS’ security-centered goals.
Yet without exception, the security features are so tightly integrated that the effect is not confusion but curiosity. Instead of confusing users with unexplained security features, the SGOS desktop invites exploration of what is probably the most original set of features seen in a distribution for some years.
Living in the land of Oz
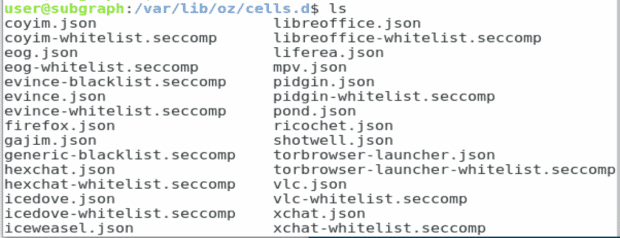
But SGOS is more than just a collection of assorted new and old security and privacy tools. For defense in depth, SGOS depends on Oz [https://github.com/subgraph/oz/wiki/Oz-Technical Details, Subgraph’s application sandbox framework. Written in Golang, applications running in Oz have seccomp-bpf policies written into them. Those policies can be viewed at /var/lib/oz/cells.d/.
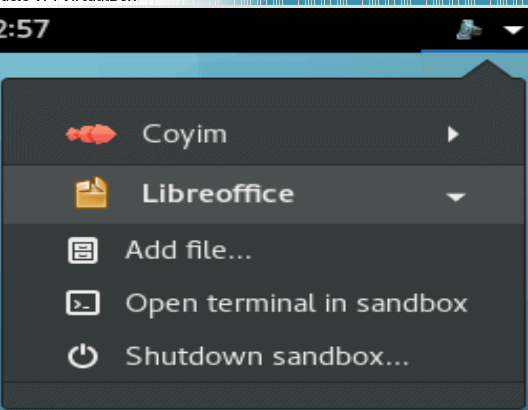
In the current release, at any rate, Oz is implemented only in the applications most likely to have interactions with other devices: CoyIM, Tor Browser, evince, eog, Icedove, and LibreOffice. Although each apparently must be run in Oz, users can start any of these tools without noticing Oz. You can see the applications currently sandboxed with the command oz list, but, more easily, you can also view from an icon in the upper right corner, which also allows users to control each sandbox individually, running a terminal in it, entering it, or closing it down.
Still in Progress
SGOS is not yet ready for everyday use. It froze several times during testing, and areas like passwords could use more attention. I could also imagine controls so that users could start their own sandboxes without leaving the desktop.
Still, even without delving more thoroughly into the back end, where the company has done much of its innovation, SGOS impresses. Although still in alpha, it proves how much more can be done to increase security and privacy simply by thoughtfully collecting a set of tools. Moreover, by placing many of these tools in the desktop, it demystifies and makes security more accessible — outcomes that, in their own way, are as important as the actual increased security.
SGOS still needs polish, but, by the time it reaches general release, it might have become the authority on how to do security the right way.
[sharedaddy]