I have been following the development of Purism‘s Librem 13 and 15 laptops for several years. Like many Linux users, I am attracted by the efforts to build secure and free systems, but hesitant about the high prices for mid-list hardware. At the very least, I would want to try before I buy. However, because that opportunity seems unlikely, the best I can do is to install PureOS, Purism’s distribution, on a virtual machine. Unfortunately, a couple of days of exploring leaves me with mixed reactions, and in the end does nothing to resolve my ambiguities.
PureOS starts off promisingly enough, being based on Debian, one of the more secure major distributions. In keeping with basic security principles, the installation is minimal (after all, how can you secure a system without knowing what is on it?), consisting chiefly of utilities and a few basic applications like LibreOffice. However, mouse movement is erratic, either because of the virtual machine or because the system is customized for Purism’s particular hardware, although an immediate software update does improve performance somewhat.
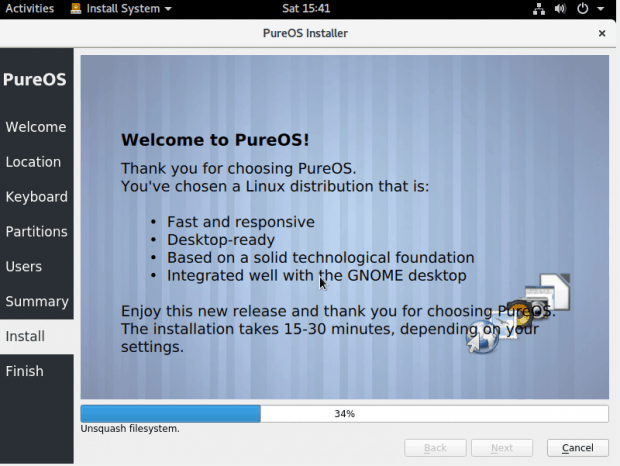 The default desktop is GNOME. As a dedicated KDE user, I usually have little interest in GNOME, but PureOS has just enough tweaks to make it interesting. For example, as in Unity, an active window’s menu is placed in the panel rather than the window’s titlebar. GNOME Classic is also supported, although in a rougher form, since in the present release, it lacks a menu. Ironically, the best system performance for me is under KDE Plasma — although, lacking information, I worry that, by abandoning GNOME, I could be forfeiting security enhancements.
The default desktop is GNOME. As a dedicated KDE user, I usually have little interest in GNOME, but PureOS has just enough tweaks to make it interesting. For example, as in Unity, an active window’s menu is placed in the panel rather than the window’s titlebar. GNOME Classic is also supported, although in a rougher form, since in the present release, it lacks a menu. Ironically, the best system performance for me is under KDE Plasma — although, lacking information, I worry that, by abandoning GNOME, I could be forfeiting security enhancements.
Root login is via sudo. Of course, this setup has been popularized by Ubuntu, but I have never seen its sense. User accounts are the ones that are most used and therefore the ones most likely to be cracked, and, under this arrangement, gaining a user’s password means gaining root access as well. Maintaining a separate root password seems more secure, provided I am careful to keep logins to root to an absolute minimum.
With such mixed feelings, I persevered, exploring PureOS, paying particular attention to security features.
A Visual Security Tour
The justification for calling PureOS a secure distribution is not detailed anywhere that I could find. The closest I could find was the generally description on the Purism website of the software being “fully auditable” — that is, completely open source — which hardly seems enough. Moreover, some security features, such as the kill-switches for the camera and wi-fi or the Librem key, are a matter of hardware, not software. Others, such as the Thunderbolt services, are only noticeable from the desktop by reading the messages at shutdown.
So what security features are visible from the desktop itself? Looking through Settings, I find some sensible defaults, such as screen-locking after five minutes, and file-sharing turned off. Although the installer says that when location sharing is permitted, an indicator is on, that, too, is apparently hardware rather than the desktop. Opening the Backup feature, I see a suggestion that automatic backups be enabled — a sensible suggestion, except that it would be more useful if it was made the first time that a user logs in, the way that Security Updates are in many distributions.
Turning to the applications, I note Boxes, a utility for managing virtual machines. Because it integrates virtual machines more tightly into the host system than, say, VirtualBox, it should make virtual machines less exposed, although I would like more details on the subject than the help makes available. However, in Thunderbird, while an Enigmail wizard is available for setting up encrypted mail, it is not enabled by default, and nothing guides a new user towards it. As for Polari, the default chat app, despite an elegant design, I could find no indication of security features whatsoever, although they might be under the hood.
In all the desktop, the most obvious security enhancements are in PureBrowser, PureOS’s modified version of Firefox. Rather than Google, the default search engine is DuckDuckGo, which claims not to track users. More significantly, PureBrowser includes the uBlock Origin plugin, which blocks popups and cookies and scripts from open sites, and displays its activity in a sidebar, which makes you realize just how much security risk lies in a common browser. The only other plugin installed by default is HTTPS Everywhere, which allows you to choose which sites to have an encrypted connection with.
It is in PureBrowser that I found what I had searching for in the rest of the PureOS desktop: visual, hands-on security. However, at least in the latest release, that fulfillment comes with a price: PureBrowser does not mimic Firefox, and, as a result, most Firefox plugins cannot be installed on it all. In one sense, this limitation is another security feature. After all, because plugins are so numerous that they are lightly vetted at best, they are an obvious security risk. However, if you depend on some plugins — for example, if you share my addiction to the advanced features of advanced browsing — you may find yourself in the age-old dilemma of finding security at odds with convenience.
Security vs. Convenience
In fact, despite Purism’s advertising, in the end I find that PureOS seems to struggle with exactly that dilemma. On the one hand, Purism’s unique tools are outstanding examples of minimal interfaces, uncluttered and easy to start using without more than the brief instructions in their windows. On the other hand, unless a lot more is hidden from users than I was able to find, PureOS seems far less a security-conscious distro than such examples as Subgraph OS or Qubes OS. Granted, Pure OS appears more secure than most major distributions, but in the dilemma between security and convenience, it seems to tip towards convenience at times rather than towards security, especially since several basic settings are left for the user to enable rather than being defaults.
If that is not the case, I wish that PureOS would do more to publicize its security features. If I were considering buying a Purism laptop, I would certainly request more information about PureOS before buying. However, based on a fairly thorough look, I am less impressed with PureOS than I hoped to be. As a security-centered distribution, it appears more of a mid-level entry than I expected from how it is promoted.
[sharedaddy]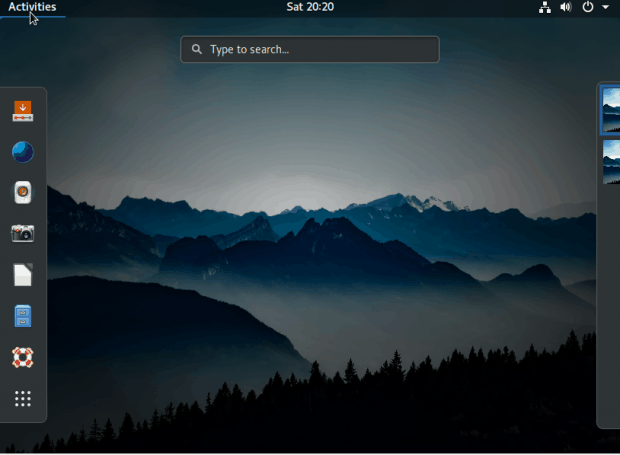



“If I were considering buying a Purism laptop, I would certainly request more information about PureOS before buying”
But what confidence do you have that you would get it?
“I wish that PureOS would do more to publicize its security features”
You do mean ‘claimed’ security features, don’t you?
The big red flag is lack of openness on a product which claims ‘security’ as its hallmark.
Doesn’t Purism realize that the only possible conclusion is that the lack of transparency is being used to cover for unsupportable claims?